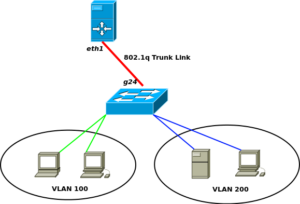
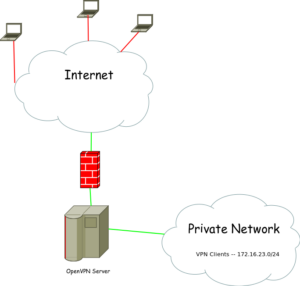
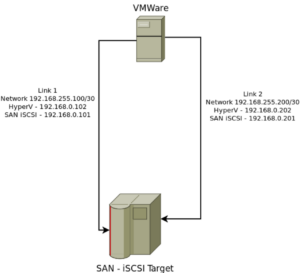
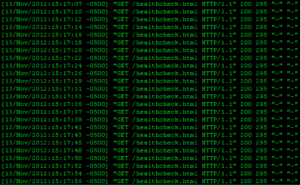
Most firewalls in the consumer world are ones that are either bought at Bestbuy or supplied by your ISP as an all-in-one type of network device. These devices, such as the Linksys WRT54GL, are good enough for most user’s home setups. Providing Wireless and Wired network access with built in Firewall security. Blocking most inbound network threats , and other unwanted requests that are not pre-established (i.e. return path from an outbound request). Some of these consumer routers can be even further enhance with a rich set of plugins and network tools by using custom firmwares. DD-WRT, Tomato, or openWRT are all interdependent communities, who develop custom firmware to be used with these consumer all-in-one routers. You can check your devices compatibility with their firmware at each of their websites.
I for one own a Linksys WRT54GL router and have used both DD-WRT and Tomato. Both of these custom firmwares as well as the stock firware(Linksys) provide enough security, accessibly, and capacity for a typical consumer. However, that’s not what this article is about! This article is how to setup your own Network Firewall using a standalone Linux box! Woot!.