An interesting question came up the other day, we have multiple endpoints sending syslogs into a F5 VIP fronting a syslog collector…all on port 514. Our logging team wanted to change the port from 514 to different ports depending on the originating endpoint. Without changing each endpoints configuration to the desired new port, we thought maybe we could do this with an iRule.
when CLIENT_ACCEPTED {
#Grab CLLIENT IP
set clientIP [IP::client_addr]
#set default syslog port
set destSyslogPort 514
#check IP against DataGroup
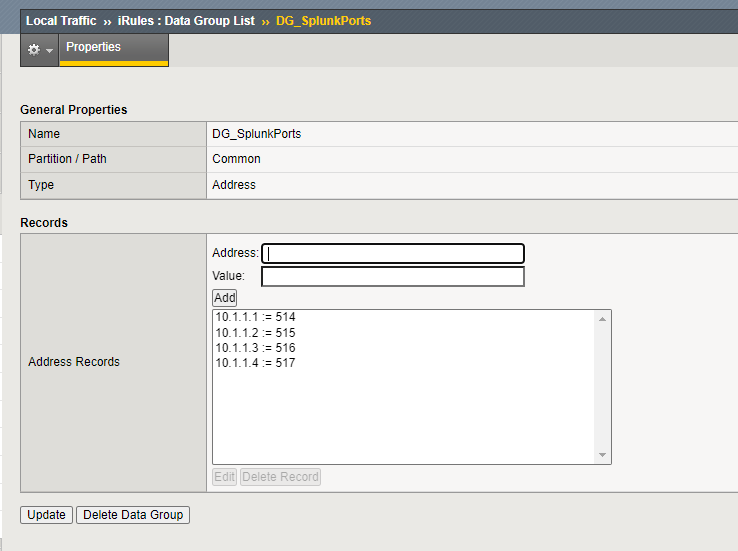
if {[class match $clientIP equals DG_SplunkPorts] } {
#get corrisponding port fro DG_SplunkPorts
set destSyslogPort [class lookup $clientIP DG_SplunkPorts]
} else {
#set as default 514
set destSyslogPort 514
}
}
when LB_SELECTED {
LB::reselect node [LB::server addr] $destSyslogPort
}
First we grab the $clientIP, as we will need this to lookup the corresponding value in the DataGroup. We also need to set the variable $destSyslogPortto 514 by default in case the $clientIPis not found…Next we use a class match statement to search for the value, if any, using the $clientIP. With the found port value, or the default, we then need to modify the LB selection process.
At this point the F5 has already chosen a backend server to load balance to, so we need to intercept this with the ‘when LB_SELECTED‘ event. Within this event we tell the F5 to ‘reselect’ the chosen backend node t, in this case [LB::server addr] which is same node already selected, cleverly retaining the same backend node selected. Lastly we set the destination port with $destSyslogPort.
DG_SplunkPorts “The Data Group Used”