Before we begin I want to clearly identify the scope of this tutorial. There are different types of VPN, we will be creating a Client VPN which implies a many to one relationship. We will have multiple clients connecting via VPN to a single OpenVPN server. This OpenVPN server will assign IP addresses to each successfully authenticated client. Using this IP Address, client’s may, depending on your network security, access devices on a private network. Effectively appearing as if the Client was directly tied into the Private Network. If you are looking for a site-to-site VPN tunnel via IPSEC this is out of the scope of this tutorial.
Our Simple Client VPN Topology
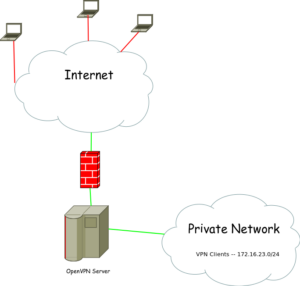
We are assuming that the 172.16.23.0/24 network has the appropriate ACLs to the resources you want VPN Clients to access.
-
Install the base packages needed
apt-get install openvpn openssl
-
Copy example confs
mkdir -P /etc/openvpn/easy-rsa/ cp -r /usr/share/doc/openvpn/examples/easy-rsa/2.0/* /etc/openvpn/easy-rsa/
-
For Ubuntu 12.04 64-bit, there is an issue with the scripts installed with openvpn.
To fix create a symbolic link for openssl.cnf file that CA scripts look for.
cd /etc/openvpn/easy-rsa ln -s openssl-1.0.0.cnf openssl.cnf
-
Change vars settings to your paticular set up.
vi /etc/openvpn/easy-rsa/vars export EASY_RSA="/etc/openvpn/easy-rsa" export KEY_SIZE=2048 export KEY_COUNTRY="US" export KEY_PROVINCE="CT" export KEY_CITY="Hartford" export KEY_ORG="techjockey.net" export KEY_EMAIL="me@myhost.mydomain"
-
Create our Certificate Authority:
- This step is necessary to create a root level trusted authority that will sign the SSL certificates/keys used by both our OpenVPN server and OpenVPN clients, during their SSL handshake. If their is no trust between either entity, their will be a SSL invalid issue, because the client trying to connect is not presenting a trusted and signed certificate. For more information on SSL please see here.
cd /etc/openvpn/easy-rsa source vars ./clean-all ./build-ca OpenVPN-CA Generating a 2048 bit RSA private key ..................................................+++ ......+++ writing new private key to 'ca.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [US]: State or Province Name (full name) [CT]: Locality Name (eg, city) [Hartford]: Organization Name (eg, company) [thejimmahknows]: Organizational Unit Name (eg, section) [changeme]:CertificateAuthority Common Name (eg, your name or your server's hostname) [changeme]:OpenVPN-CA Name [changeme]:CertAuth Email Address [mail@host.domain]:
-
Create Server Cert and Key, signed by CA:
Notice, in the next step, how we are signing the OpenVPN server’s Certificate and Key with our Certificate Authority certificate from the previous step!
cd /etc/openvpn/easy-rsa source vars ./build-key-server OpenVPN-Server Generating a 2048 bit RSA private key .....................................................................................+++ ............+++ writing new private key to 'OpenVPN-Server.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [US]: State or Province Name (full name) [CT]: Locality Name (eg, city) [Hartford]: Organization Name (eg, company) [thejimmahknows]: Organizational Unit Name (eg, section) [changeme]:OpenVPN Server Common Name (eg, your name or your server's hostname) [OpenVPN-Server]: Name [changeme]:OpenVPN Service Email Address [mail@host.domain]: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: Using configuration from /etc/openvpn/easy-rsa/openssl.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'US' stateOrProvinceName :PRINTABLE:'CT' localityName :PRINTABLE:'Hartford' organizationName :PRINTABLE:'THEJIMMAHKNOWS' organizationalUnitName:PRINTABLE:'OpenVPN Server' commonName :PRINTABLE:'OpenVPN-Server' name :PRINTABLE:'OpenVPN Service' emailAddress :IA5STRING:'mail@host.domain' Certificate is to be certified until Nov 13 19:22:27 2022 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
- Create Client Certificate/Key Pair and sign by CA:
cd /etc/openvpn/easy-rsa source vars ./build-key thejimmahknows_vpnclient Generating a 2048 bit RSA private key .......................+++ ...................+++ writing new private key to 'thejimmahknows_vpnclient.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [US]: State or Province Name (full name) [CT]: Locality Name (eg, city) [Hartford]: Organization Name (eg, company) [THEJIMMAHKNOWS]: Organizational Unit Name (eg, section) [changeme]: Common Name (eg, your name or your server's hostname) [thejimmahknows_vpnclient]: Name [changeme]:jim Email Address [mail@host.domain]: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: Using configuration from /etc/openvpn/easy-rsa/openssl.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'US' stateOrProvinceName :PRINTABLE:'CT' localityName :PRINTABLE:'Hartford' organizationName :PRINTABLE:'THEJIMMAHKNOWS' organizationalUnitName:PRINTABLE:'changeme' commonName :T61STRING:'thejimmahknows_vpnclient' name :PRINTABLE:'jim' emailAddress :IA5STRING:'mail@host.domain' Certificate is to be certified until Nov 13 19:24:19 2022 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
-
Create Diffie Hellman Key Exchange:
./build-dh
-
Change to Keys Directory
So we just created a Certificate Authority certificate and key pair, a Server certificate and key pair signed by our CA, and a Client certificate and key pair signed by our CA. The scripts you just ran place the certificates and keys in the /etc/openvpn/easy-rsa/keys directory . Navitgate to this directory. You may notice that you need to be root user in order to change to this directory…Don’t worry that is a good thing! Do an ls -l so we can see what’s in this directory…we should see the following:
cd /etc/openvpn/easy-rsa/keys ls -l ca.key ca.crt OpenVPN-Server.crt OpenVPN-Server.key thejimmahknows_vpnclient.crt thejimmahknows_vpnclient.key
NOTICE: We have to files per entity. a CRT and a KEY, it is very important that the KEY is only readable at the root level and only resides on the entity. You should not, I repeat not have the entity’s KEY in multiple locations.!!
-
Copy Client files to Client device
Copy the Client’s CRT and KEY to it’s device. You will also need to copy the ca.crt certificate to the Client’s device. (This is due to the fact that the CA we created is self-signed and is not a public third party Certificate. Anyway..) Remember when the CRT and KEY are on the Client’s device, make sure the KEY is read-only by a root user.
-
Identify Server side files
Make note on our OpenVPN server the location of the following; ca.crt, dh2048.pem, OpenVPN-Server.crt, and OpenVPN-Server.key. We will need their full path for the next step
-
Copy a sample server configuration file:
cp /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz . gunzip server.conf.gz
-
Edit the server.conf file and change/add the following:
vi server.conf port 1194 proto udp #cert information ca /etc/openvpn/easy-rsa/keys/ca.crt cert /etc/openvpn/easy-rsa/keys/OpenVPN-Server.crt key /etc/openvpn/easy-rsa/keys/OpenVPN-Server.key dh /etc/openvpn/easy-rsa/keys/dh2048.pem #sets IP range and subnet to assign VPN clients after they successfully connect and negotiate. Or your VPN range here. server 172.16.23.0 255.255.255.0 #maintain a record of clients and their virtual IP address, so they are assign the same one every time. ifconfig-pool-persist ipp.txt #push statements, push routing and other broadcast information to a client when they ask to get an virtual IP. Push your DNS and route information relative to your infrastructure. Here is where you would want to put your DNS server clients should use to resolve resources on your networks. push "dhcp-option DNS 208.67.220.220" push "dhcp-option DNS 208.67.222.220" #do you want VPN clients to be able to talk to each other? client-to-client #keepalives keepalive 10 120 #enable compression (has to be done on both sides to work) comp-lzo #status file (different than logging, show user virtual IP associations, etc). Handy. status openvpn-status-log #log stuff log /var/log/openvpn.log verb 3
-
Restart the OpenVPN service on the server.
service openvpn restart
-
Client Configuration
On your client, assuming Ubuntu OS is running on your client. Install the necessary packages for the OpenVPN Client
apt-get install network-manager-openvpn
After an OpenVPN option should be available in Network Manager, remember where your Client’s certificate and key are stored, then go to Edit Connections and the VPN Tab.
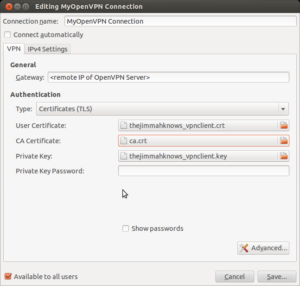
Now fill in the information necessary, Connection name, Gateway (which is your OpenVPN Server IP or DNS), User Certificate is your client CRT, CA Certificate is the ca.crt, and Private Key si the KEY file. See picture for example.
The new connection should now appear in your Network Manager list of connections.
- Congratulations! You just set up a Client VPN Server and got a Client connecting over a secure SSL tunnel. Woot!
Sources:
- https://help.ubuntu.com/community/OpenVPN
- https://help.ubuntu.com/community/VPNClient
- http://ubuntuforums.org/showthread.php?t=1134459&page=4
for ubuntu Network Manager OpenVPN client not working with split tunneling.