I originally discovered Adblock Plus when I first downloaded Firefox many years ago. Since then I’ve installed the Adblock plugin right after Firefox, etc. It’s become so standard that I almost think Firefox should just bundle them together. Including it in it’s default install exe.
Adblock Plus works as if it were a local content policy, filtering each request you make with Firefox. Each URL, each domain, each link you navigate to is check based on a static blacklist of expressions and URLs. If a match is found, Adblock Plus simply discards the content from rendering. The discarding and allowing content to load is managed by the Content Policy engine within Firefox. Adblock Plus simply utilizes this in order to block the unwanted contents. Or at least this is my comprehension of how it works. :-p
Setting up your own Network wide Adblocker
The purpose of this guide and tutorial is to instruct you on how to set up your own network based adblocker. Expections after completion is every client browser on the network will benefit from adblocking. I will include as much as possible, and feel free to ping me with questions or comment down below.
You will need:
- Computer that will be running the Web Proxy. (For this article, see specs below)
- OS that will host the Proxy Software. (For this article, Ubuntu 12.04 32-bit Server)
- Proxy software that allows rewrite engines/programs. (squidGuard)
- Content-Control-Software or URL Redirect Application(This will consume your blacklists)
- URL and RegExp Blacklists consumable by your Content-Control-Software (Here are some free ones)
- Optional: ipTables for transparent proxy redirection
- Patients and enthusiasm :-p
Step 1: Installling OS and software
- Spec’ing out your hardware. Keep in mind your sizing and scope of clients you will be serving
For this tutorial I used the following:
–Dual Core -Intel(R) Xeon(TM) CPU 2.66GHz 32-bit
–4GB DDR RAM
–320GB SATA HD
–Dual 10/100/1000 NIC - Download a ISO copy of Ubuntu or Debian.
- Install Ubuntu, for tutorial see here.
- Make sure you are a sudo users or have root access, needed for the next steps.
- After Install update your system to the latest via
sudo apt-get update && sudo apt-get upgrade -y
- Next install squidProxy
sudo apt-get install squid3 -y
- Install squidGuard from the repositories
sudo apt-get install squidGuard -y
- Setting static IP address on the server. Do a
ifconfig eth0to figure out what your current IP is. Mine was 192.168.0.113. We will assume this is a /24 network, so pick a lower number for the last octet. I chose 192.168.0.5. Reason for this is out side the scope of this article. Perform the static ip address config.
Add the following insudo vi /etc/network/interfaces auto eth1 iface eth1 inet static address 192.168.0.5 netmask 255.255.255.0 - Restart network interfaces. Make sure you are local, you will lose remote access!!.
sudo /etc/init.d/networking restart
- Check
ifconfig eth0you should have 192.168.0.5(or the IP you picked).
***The base installation is now complete and we are now ready to configure our service applications!
Step 2: Configuring squidProxy
- Make a copy of your default config file.
sudo cp /etc/squid3/squid.conf /etc/squid3/squid.conf.bak
- Null the squid.conf file.
sudo su - cat /dev/null > /etc/squid3/squid.conf
- Edit the squid.conf vith vi and paste the following lines.
sudo vi /etc/squid3/squid.conf #acl lists acl manager proto cache_object acl localhost src 127.0.0.1/32 ::1 acl to_localhost dst 127.0.0.0/8 0.0.0.0/32 ::1 acl localnet src 192.168.0.0/24 # RFC1918 possible internal network #port connections acl SSL_ports port 443 acl SSL method CONNECT acl Safe_ports port 80 # http acl Safe_ports port 21 # ftp acl Safe_ports port 443 # https acl Safe_ports port 70 # gopher acl Safe_ports port 210 # wais acl Safe_ports port 1025-65535 # unregistered ports acl Safe_ports port 280 # http-mgmt acl Safe_ports port 488 # gss-http acl Safe_ports port 591 # filemaker acl Safe_ports port 777 # multiling http acl CONNECT method CONNECT #allow/deny http_access allow manager localhost http_access deny manager http_access allow localnet # Deny requests to certain unsafe ports http_access deny !Safe_ports # Deny CONNECT to other than secure SSL ports http_access deny CONNECT !SSL_ports # Example rule allowing access from your local networks. http_access allow localnet http_access allow localhost # And finally deny all other access to this proxy http_access deny all #bind address default port is 3128 http_port 192.168.0.5:8080 #cache directory cache_dir ufs /home/serveruser/squidcache/ 512 16 128 cache_mem 2048MB #coredump_dir /home/serveruser/squidcache/ #log cache_store_log /var/log/squid3/store.log
- Next start the service up.
sudo service squid3 restart
- If you encounter any issues or error message, check the syslog
less /var/log/syslog
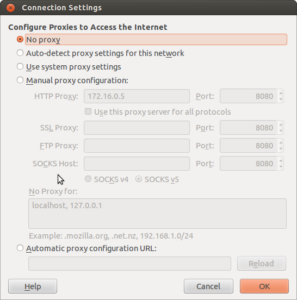
- TEST with Firefox. Go into Firefox settings –> Connection Settings. Enter in the IP address and Port of your proxy server. Similar to this
 Try to browse to some sites like Google, MSN, Facebook, etc. Ensure you can get to them. Next, to make this a thorough test and ensure you are connecting through the proxy. Go back to your Proxy server’s terminal. Enter the following to turn off the proxy service.
Try to browse to some sites like Google, MSN, Facebook, etc. Ensure you can get to them. Next, to make this a thorough test and ensure you are connecting through the proxy. Go back to your Proxy server’s terminal. Enter the following to turn off the proxy service.
sudo service squid3 stop
After that completes try to navigate and browse on the client machines. You should get an error.
***Congratulations you have successfully set up your first Proxy Server with squidProxy!!!
Step 3: Configuring squidGuard and Blacklists
- Make a backup of the squidGuard config file.
sudo cp /etc/squid3/squidGuard.conf /etc/squid3/squidGuard.conf.bak
- Grab a blacklist from here.
cd ~ && wget http://squidguard.mesd.k12.or.us/blacklists.tgz
- Uncompress.
tar xzvf blacklists.tgz
- This Uncompresses the folder structure for all the blacklists categories, i.e. Ads, Porn, Gambling, etc. We are only concerned with Ads, so grab it’s path.
cd blacklists/ads/ pwd
COPY this path, need it for later.
- We have to make these blacklists readable by the user that squid runs as.
cd ~ && sudo chown -R proxy.proxy blacklists sudo chmod -R 750 blacklists
I had to use the permission bits of 750, it was the only permissions that would allow squid to read the blacklists. I put a 0 at the end because I don’t want the list readable by any other users on the system.
- Now time to edit the squidGuard.conf file.
sudo vi /etc/squid3/squidGuard.conf dbhome /home/serveruser/squidGuard logdir /var/log/squid3 #create ads category dest ads { #location of blacklists, domains, urls, expressions. domainlist blacklists/ads/domains urllist blacklists/ads/urls expressionlist blacklists/ads/expressions } acl { default { #allow except 'ads' pass !ads all #redirect to transparent gif redirect http://localhost/blank.gif } } - Now add the squidGuard specific’s to the squid.conf file, so the main squid process is aware of squidGuard. Add these lines to the end of your squid.conf file.
sudo vi /etc/squid3/squid.conf #rewrite program squidGuard url_rewrite_program /usr/bin/squidGuard -c /etc/squid3/squidGuard.conf url_rewrite_children 5 #threads url_rewrite_concurrency 0 #jobs per threads
- Initialize the squidGuard database files, to consume the blacklists you just downloaded. Needs to be done everytime you update the list.
sudo squidGuard -C all
Should be fairly quick, if it hangs, squidGuard probably cannot read the blacklist directory. Check your syslog.
- For the next step I recommend having two terminal windows open to your proxy server. This will make it easier to tail the logs when you try to start it for the first time.
- Restart squid3 to pick up the new configuration items(i.e. squidGuard) Make sure you tail your syslog with the other window.
sudo service squid3 restart
In your squidGuard log you should see the following lines:
less /var/log/squid3/squidGuard squidGuard 1.4 started squidGuard ready for requests
You will also see in the log how it loaded the dbfiles you defined in your squidGuard.conf file.
- Testing. Ensure your client’s firefox still has Connection Settings pointing at your proxy server. Now browse to a website that has a lot of ads. I suggest p2p sites, usually utilize a crap load of ads.
***Congratulations you have protected your network from ADs!!!
Optional Step 4: Transparent Proxy Redirection via iptables (optional)
-
- This next section assumes you have a working IPTables setup, with a Router/Firewall at 192.168.0.1 and a Proxy Server at 192.168.0.5
- Need to add two statements.
sudo iptables -A PREROUTING -i eth0 -p tcp -m tcp --dport 80 -j DNAT --to-destination 192.168.0.5:8080
- ***NOTICE We are only specifying port 80, not 443!
Port 443 bypasses the proxy as we are not doing SSL Interception.
- Now we must tell squidProxy about the transparency. Find the line http_port and add transparent to the end of it.
http_port 192.168.0.5:8080 intercept
- Remove Firefox proxy settings in Connection Settings.
***Congrats you are now transparently redirecting all port 80 calls to your proxy server.
Sources:
- Adblocker FAQs http://adblockplus.org/en/faq_internal
- Ubuntu Server Installation Guidehttp://ubuntuserverguide.com/2012/05/how-to-install-ubuntu-server-12-04-lts-precise-pangolin-included-screenshot.html
- Installing Squid http://www.server-world.info/en/note?os=Ubuntu_12.04&p=squid&f=3
- squidGuard Config site http://www.squidguard.org/Doc/configure.html
- squidGuard Examples http://www.squidguard.org/Doc/examples.html
- Ubuntu Specific squidGuard Config https://help.ubuntu.com/community/SquidGuard

Fantastic. I had already setup squid transparently over the weekend, and this worked for setting up squidguard, with a few variations: my squid install directory was squid, not squid3 and the squidguard.conf edit (a) domainlist blacklists/ads/domains & urllist blacklists/ads/urls should be [folder you copied from pwd]/ads/domains .. & (b) the blacklist source you gave has no expressions (so comment that line out). Finally, Step 4 needs to happen on the router, correct?
Correct. the IPTABLES portion takes place on your router, if you are using IPTABLES. This can be done on other Firewal platforms as well.
Hello, I was just reading this (http://ispltd.org/server_guides:squid_black_list) and thought I would take the time to write a short note to inform you all that we offer blacklists tailored specifically for Squid proxy native acl, as well as alternative formats for the most widely used third party plugins. So we invite you all to check us out. We take a great deal of pride in the fact that our works offer a higher degree of quality than the freely available options. Our lists are also compatible with UrlFilterdb.
Quality Blacklists Tailored For Squid Proxy – http://www.squidblacklist.org
Thanks for the tutorial but during my setup, after step 2, my browser says ‘firefox is configured to use a proxy server that is refusing connections.’ Please assist. Thank you
Step 2 simply blanks the squid.conf file so you may paste in the contents of step 3. Try that and let us know. Thanks!