**Updated 2.0.1 (rc1)**
Hey all, due to the success of the Blocklist2ACL.hta script from this previous post, I decided to port the code over from VBscript to Java. In effort to make the program more stable, cross-platform comparable, and future proof. I’ve received a few comments and PMs from users explaining that the Internet Explorer requirement was giving them issues. This is true, the old script relied heavily on Internet Explorer and what version you were running. Well enough of that, as I was able to port the code over to Java (no, not JavaScript), which has it’s own runtime objects and classes that I was able to utilize.
Requirements:
JRE1.7+, grab it here.
Download:
Blocklist2ACL20rc1
SHA1 = 9DD863BBF0A5BC2EE110EF6C6F899F7AAC2A0ABD
SHA-256 = 245CA6DE2A93800742BD16B6506C6C3241A9E62410E294B76734875AB89A636C

Works great & even better bc it runs on linux now! Thank you very much!!!
On a side note, watchguard firewalls allow manual block lists imported from .txt files in the following format:
160.240.0.0/16
160.255.0.0/16
161.59.0.0/16
161.66.0.0/16
161.71.0.0/16
161.189.0.0/16
161.232.0.0/16
162.211.236.0/22
Any chance you could add an option for watchguard’s or similar?
Glade to hear! Is the Format for watchguard the same across all their models? and do you know what the command statement would be for an access-list? I could try adding it to the code as a potential option.
Jim, its the same across all models. All you do is import a list like the one above, no command statement. Those address are imported into the blocked site list. So all you need is ip and subnet in slash format
I have 1 at home to try it on
Cool! Give me a few days and I’ll try to work it into the app.
Jim,
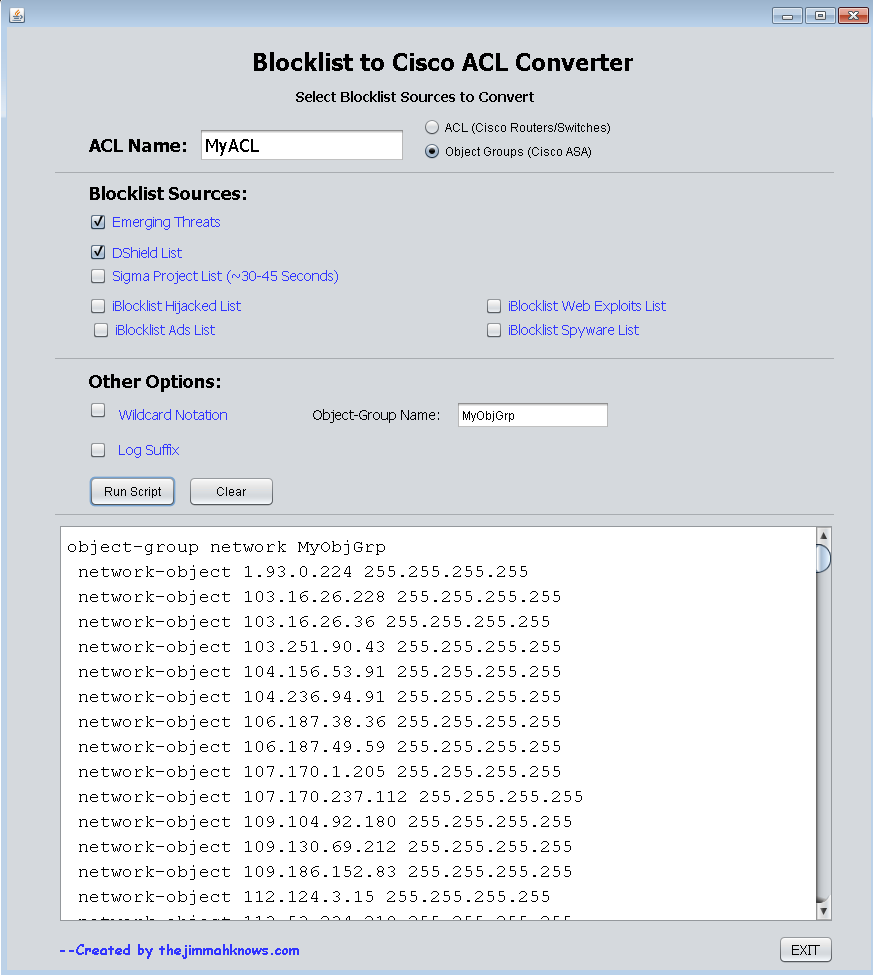
I noticed the log suffix is not working. I have applied the list to my ASA and it doesnt seem to be blocking.
I ran the following (I shortened the MyObjGrp list so the post wasnt too long):
conf t
object-group network MyObjGrp
network-object 1.93.0.224 255.255.255.255
network-object 103.16.26.228 255.255.255.255
access-list MyACL extended deny ip object-group MyObjGrp any
access-group MyACL in interface outside
I then tried to browse to 1 of the listed ips from internally and was able to connect to one of the sites. I then added my home ip to the block list and tried to VPN into the ASA and was able to. I was thinking since I am able to browse out to the sites internally, perhaps if I add my home ip to the blocklist and try to access the ASA I would be blocked. Am I applying the list correctly?
Correct, assuming you have a simple (inside,outside) topology. When you egress out you are going from a higher-security level(inside) to a lower one(outside) which is allowed. What this means is connections originating on your inside network will be able to connect to these IPs. Also the ACL you are assigning to your outside interface via the access-group statement will only be applied to connections originating from the outside coming in…
If you want to prevent inside users from connecting to these IPs you would have to create another ACL and assign it to an access-group on your inside interface. Doing so may make this more complex than you want, since adding a ACL to your inside access-group, you will have to explicitly allow everything you want y our inside users to be able to access…Can get out of hand, but up to you..
I will look into the log issue and adding the WatchGuard ACL output. I haven’t been able to find time to code because of the holiday coming up…
No rush and thanks for the quick response
Why would I still be able to VPN in from my home ip if I added my home ip to the block list for testing though?
Hmm. Must have something to do with the ASA’s order of operations. I bet when enabling remote VPN it allows those ports through, regardless of your ACL. I will have to do more research to confirm though.
Could you post your configuration…?
Sorry, I had to revert as the ASA I was trying (5510) was maxing out. So I had to revert.
I will retry this week and post
Hey Gerry, I found this site http://www.ipdeny.com/ipblocks/ that provides Blocklist based on Geographic location. I was thinking of incorporating into version 2.1!
Hey Gerry, try incorporate firehol_level1 and other firehol ip list.
I’ve changed to uloaded.net who claim to not expire their user’s file uploads. Try again please.