Hi All, been awhile since my last post, however I believe this to be a good one!. So…the question arose the other day regarding NAT-Traversal. What is that? Why do we have it? What does it do? Most network engineers have heard of NAT-traversal before when configuring their Firewalls and VPN Clients, etc. But, I wanted to take a minute to explain where NAT-Traversals (NAT-T) need came from and the reason we still use it.
In order to understand NAT-Traversal, we need to understand two Networking concepts. First we need to understand “The Network Flow”. HOw do two hosts on a Network maintain a communication session. The second, is Network Address Translation. Yes NAT’ing, is a big part of IPv4 networks, they are so common place that you are probably using NAT’ing right now when reading this article.
The Network Flow.
So in a typical end-to-end connectivity the network traffic flow is maintained by 4 main parameters.
- Destination IP
- Destination Port
- Source IP
- Source Port
These 4 parameters provide a seamless flow of packets back and forth to each end-to-end device within a communication. It is how packets carrying your data arrive at their destination and it is how a return response knows how to get back to the requesting device. The IP requirement is usually pretty straight forward, it’s like the address of a house. You have to know the TO and FROM fields when sending a mail letter. So where does this port information come into play?? So Port number is like a sub-address of where the mailbox is located on a house. Usually a home will only have one mailbox, but imagine the same scenario with an apartment building or housing complex..Many mailboxes at a single address. Now depending on where you live you may need to prepend or add a apartment number to the address. Translate this same concept to port numbers. If my address is 123 North St and I am sending to 789 South St. My courier knows how to drive to each destination, but it doesn’t know where to put the actual mail envelopes since it is an apartment building with hundreds of apartments. This is where the port number comes in. So if on my envelope I put 123 North St. Apt#100 and I am sending to 789 South St. Apt#201. My mail will be delivered not only to the correct address but the correct mailbox.
I like using the apartment analogy, because it makes us think about Address and Ports being used together to deliver mail. An address and port combination is called a Socket in the networking world.
Now in a typical request scenario, a client forms the TCP/IP datagram. A Client’s machine fills in the destination IP and Destination Port based on the target and application type generating the request. For example, when you type http:// in your browser, the browser application knows to use port 80 as the Destination Port. The client then fills in it’s own IP address for the Source IP, and the OS chooses a Source Port at random. We call this random Source Port, the Ephemeral Port.
A typical TCP/IP communication header.
Sent Packet:
| Dst IP | Dst Port | Src IP | Src Port |
| 192.168.10.10 | 80 | 192.168.1.100 | 49152 |
Return Packet:
| Dst IP | Dst Port | Src IP | Src Port |
| 192.168.1.100 | 49152 | 192.168.10.10 | 80 |
A Brief NAT’ing Lesson
How this works is a Network device in-between the source and destination networks, usually a Router or Firewall, performs Network Address Translation. When NAT’ing occurs the Network(Router or Firewall) device needs to maintain what has been translated, so it can be untranslated when it returns. The Network(Router or Firewall) device performing the NAT’ing creates it’s own local table of addresses it has translated. It maintains the identification of which packets have been translated by taking into account the random source port from above. Remember the Ephemeral Port. This random source port is easy way for the Network device to keep track of open connections being translated.
NAT’ing Example #1. In this example I am showing a packet before it passes through a router performing NAT’ing, “untranslated”, and showing a packet after it passess through a router performing NAT’ing, “translated”. Translating Source IP from 192.168.1.100 to 2.2.2.2)
Untranslated Packet
| Dst IP | Dst Port | Src IP | Src Port |
| 8.8.8.8 | 80 | 192.168.1.100 | 49152 |
Translated Packet
| Dst IP | Dst Port | Src IP | Src Port |
| 8.8.8.8 | 80 | 2.2.2.2 | 49152 |
NAT’ing Example #2. In this example I am showing how a router performing the NAT’ing maintains a NAT table of packets it has translated and untranslated. The example below also shows different Source IPs connecting to the same Destination IP. These Source IPs will need to be translated to a different address, 2.2.2.2.
Local NAT Table
| Original Source IP | Translated Source IP | Source Port | Destination IP | Destination Port |
| 192.168.1.100 | 2.2.2.2 | 49152 | 8.8.8.8 | 80 |
| 192.168.1.101 | 2.2.2.2 | 49943 | 8.8.8.8 | 80 |
| 192.168.1.102 | 2.2.2.2 | 49563 | 8.8.8.8 | 80 |
| 192.168.1.104 | 2.2.2.2 | 49234 | 8.8.8.8 | 80 |
Notice: The Soure Port is unique to each original IP. Both the Source IP, Source Port, and Destination IP and Destination Port are used together to maintain the Translation table, allowing the correct packets to be untranslated on their return. Sounds similar to “The Network Flow” from above right?
The problem.
In world of IPSEC, we do not use TCP or UDP protocols, in fact we use a completely different Network Layer Protocol(ICMP,ESP, OSPF, RIP,EIGRP,etc) instead of a Transport Layer Protocol (TCP/UDP). In fact, the protocol is used to protect and hide the original IP information, which is the whole point of IPSec. IPSec uses an encapsulating protocal called Encapsulating Security Payload(ESP) to take the original IP information and securely encasulate it via encryption. This prevents wire-tapping or network sniffers from discovering the original IP information while it is in transit. This ESP protocol includes only a Source IP, Destination IP, and a ESP Header and Footer to maintain session state information. No TCP/UDP port information can be used to create a NAT table binding!!!
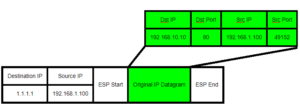
Notice: There is no TCP/UDP Port information!! It has been replaced by the ESP protocol.
The issue arises, when a Client attempts to initiate an ESP connection behind a network(Router or Firewall) device that performs Network Address Translation (NAT). NAT’ing involves the manipulation of the IP Header and TCP/UDP port information to maintain sessions states as stated in the above section. The Network(Router or Firewall) device is unable to maintain a unique translation state with these packets and therefor a IPSec tunnel cannot be formed.
The Solution:
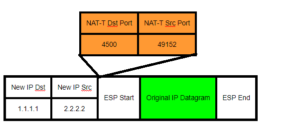
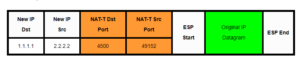
NAT-Traversal to the rescue!! NAT-Traversal encapsulates the datagram yet again with a UDP Packet. By doing so, the Packet now includes a Destination Port and Source Port! We can now successfully perform NAT’ing and maintain the connection state in the NAT table.
NAT-T Dst/Src port added to original ESP datagram:
VPN Passthrough
I wanted to mention this feature, because it is very common among home routers utilizing Network address translation. VPN Passthrough is a Consumer router specific technology, used by Routers that cannot support VPN technologies natively. Meaning the router does not perform VPN, the client’s computer does. Such as a VPN Client, etc. The original issue of NAT’ing a ESP packet is still present, however the router does not support NAT-Traversal. If VPN Passthrough is enabled on the consumer router, the router inspects VPN traffic originating from it’s internal network devices and maintains a table similar to the NAT-T table, but via some other propritary means.
The Requirement.
Both ends need to support NAT-Traversal, since a UDP port is used instead of the ESP Layer 3 protocol. NAT detection also takes place at the start of a IPsec communication, called NAT-discovery. If during NAT discovery, NAT-Traversal is not detected, the IPSec will not be brough up over NAT-Traversal and will use straight ESP.
Configuring NAT-Travesal on a Cisco ASA 5500
ASA# config terminal ASA(config)# crypto isakmp nat-traversal 20 exit
Configuring NAT-Travesal on Openswan
openswan# vi /etc/ipsec.conf config setup nat_traversal = yes
Notice: This will enable NAT-Traversal globally on the ASA, but remember both sides have to agree and support NAT-Traversal for it to actually work and be used.

Nice write up dude. Thanks.
Very nice and helpful write-up. Thanks!
Clear and concise, thank you.
Good One..!!!
Can you also explain how packet is processed when NAT-T encapsulated packet reaches the NAT Router/Firewall
Hi Suraj,
The NAT-T packet is handle like any PAT device your firewall is managing. For Cisco the mapping is stored in the xlate table.
nice article awesome
Hi there ,
Thank you so much for this article.
I have a question tough : isn’t 4500 the source and destination port ?
Regards
Correct. I believe as the PAT mechanism on your FW will change the source port as the packet leaves so it knows how to map it on return.